Gameover Zeus, a powerful virus that has been in the wild since 2011 and responsible for extorting as much as US$100m from members of the public, is being targeted by a concerted international police effort led by the FBI.
GameOver Zeus which steals bank information and sends it to overseas hackers, is a Trojan virus that siphons passwords from online banking sites through Windows computers.
Once inside a computer it quietly tracks each keystroke used to log into a bank account.
The US government and various private industry players including Dell, Microsoft and Symantec targeted a group of hackers based in the US, Russia and Ukraine in a stealth attack code-named ‘Operation Tovar’.
The GameOver Zeus virus is believed to be the brainchild of Syrian-born Evgeniy M. Bogachev, of Anapa, Russia.
Bogachev is also believed to be responsible for the CryptoLocker virus that spreads through emails that look like they are legitimate notices from FedEx or UPS.
As Cryptolocker spreads the software encrypts the machine and then demands a ransom of typically US$500 or its equivalent in Bitcoin to release the machine.
The FBI estimates that nearly 250,000 computers worldwide have been infected by CryptoLocker and payments of more than US$27m have been extorted by the hackers from the public.
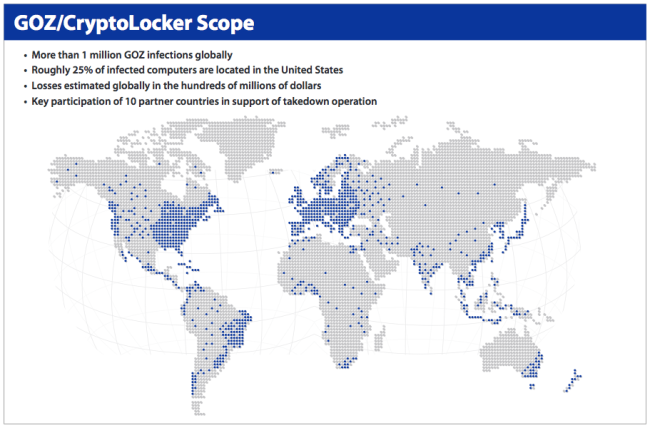
It is also estimated that up to1m machines have been infected with GameOver Zeus.
An extremely sophisticated type of malware
“GameOver Zeus is an extremely sophisticated type of malware designed specifically to steal banking and other credentials from the computers it infects,” the FBI explained.
“It is predominately spread through spam e-mail or phishing messages.
“Unbeknownst to their rightful owners, the infected computers become part of a global network of compromised computers known as a botnet—a powerful online tool that cyber criminals can use for their own nefarious purposes. In the case of GameOver Zeus, its primary purpose is to capture banking credentials from infected computers, then use those credentials to initiate or re-direct wire transfers to accounts overseas that are controlled by the criminals. Losses attributable to GameOver Zeus are estimated to be more than US$100 million.”
The FBI, the European Cybercrime Centre and agencies in 10 countries around the world, including the UK, the Netherlands, Germany, France, Italy, Japan, Luxembourg, New Zealand, Canada and Ukraine, coordinated to crack down on the criminal gang.
Bogachev remains at large but currently facces up to 14 criminal charges as the ringleader of the gang.
The GameOver Zeus investigation, according to U.S. Deputy Attorney General James Cole, combined “traditional law enforcement techniques and cutting edge technical measures necessary to combat highly sophisticated cyber schemes targeting our citizens and businesses.”
Small businesses in the eye of major cyber storm
“Never before have we seen this scale of co-ordination between the NCA and the FBI to stop one cyber-attack, and it’s very exciting for the industry and businesses,” said Jason Steer, director of Technology Strategy, FireEye.
“It’s these kind of incidents that also strike the everyday public into action too. Everyone needs to make the most of this rare window of opportunity to protect themselves from this crimeware (CyptoLocker and GOZeus) before the attack evolves and cyber criminals try and get back into your computers and data by another means.
“For individuals, don’t underestimate how important simple things like updating all your software and applications which will help to protect you. Installing the most up-to-date anti-virus engines and signatures, that should have the relevant detection and removal tools to help you remove the crimeware, will also protect you from any variants relating to it in the future.”
Steer said that small companies are also a big target because they won’t necessarily have the resources readily available to combat this form of cyber attack.
“The basics steps will help with prevention but attacks like CyptoLocker and GoZeus are incredibly powerful so businesses need to understand the information that is most critical to their business and prioritise its protection. Back it up regularly and protect it with use of firewalls, two factor authentication and other techniques that will slow down attackers and make them move on elsewhere.
“Cyber criminals are evolving and this is just the next wave of how they can monetise what they do. We all need to know what is important to us and keep it safer and better protected,” Steer said.
Cyber criminal image via Shutterstock