Syrian President Bashar al-Assad’s forces are using booby-trapped fake femme fatales to steal vital battlefield information from lonely opposition fighters on the battle lines in Syria, according to FireEye.
Vital information such as the weapons, dispositions of troops and the names and birthdates of fighters are being stolen as part of a sophisticated hacking operation by al-Assad’s forces.
According to cybersecurity player FireEye, hackers posing as women stole a cache of critical documents and Skype conversations revealing the Syrian opposition’s strategy, tactical battle plans, supply needs and troves of personal information.
They ensnared their victims by posing as sympathetic and attractive women.
A female avatar would strike up a conversation on Skype and exchange a personal photo with her target.
Before sending the photo she typically asked which device the victim was using – an Android smartphone or a PC – in order to send the appropriately tailored malware.
Once the target opened the photo – laden with malware – the hackers were able to select and steal the data they required, including Skype chat logs and contacts.
As a result, the threat group was able to amass a significant amount of data from Skype account databases, including planning documents, spreadsheets and photos.
The hackers stole a range of information, including lists of fighters, pictures of suspected Hezbollah operatives and whole sets of files pertaining to upcoming large-scale military operations, including satellite images, battle maps, geographic co-ordinates and details such as the amount of Kalashnikov rifles and light machine guns captures.
“In one chat, opposition members discuss the movement of a shipment of 9M113 TOW missiles and launchers, and agree upon a time and location to hand over the weapons,” FireEye revealed.
The hacker also stole political information, as well as material concerning humanitarian activities in Syria and bordering countries.
“Unlike other threat activity that we have profiled, this is not just cyberespionage aimed at achieving an information edge or a strategic goal,” FireEye said.
“Rather, this activity, which takes place in the heat of a conflict, provides actionable military intelligence for an immediate battlefield advantage. It provides the type of insight that can thwart a vital supply route, reveal a planned ambush, and identify and track key individuals.
“This intelligence likely serves a critical role in the adversary’s operational plans and tactical decisions. However, this tactical edge comes with a potentially devastating human cost.”
A warning to us all
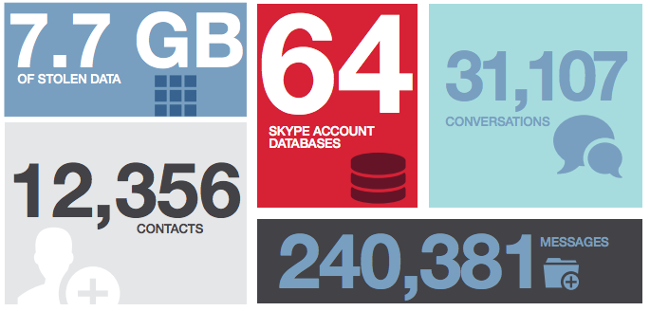
In all, 7.7GB of data is said to have been stolen by hackers between November 2013 and January 2014, encompassing 64 Skype account databases, with 31,107 conversations, 12,356 contacts and 240,381 messages.
According to security expert Graham Cluley, the fact soldiers on the frontlines of a battlefield could be easily compromised by strangers online is a warning to us all.
“Of course, the warning to be suspicious of strangers contacting you out of the blue on Skype and other chat services isn’t just relevant to military forces in Syria. It’s sensible advice for anybody on the internet.
“If you are ever approached – be it on Skype, email or Facebook – by a stranger who shows an odd interest in you, be on your guard. That next file or link they send you could be malicious.”
FireEye is a Silicon Republic Featured Employer, comprised of top tech companies that are hiring now