While business social network LinkedIn is reporting there have been no compromised LinkedIn accounts as a result of the theft of passwords on 6 June, a new infographic examines whether or not the site’s members were using known bad passwords.
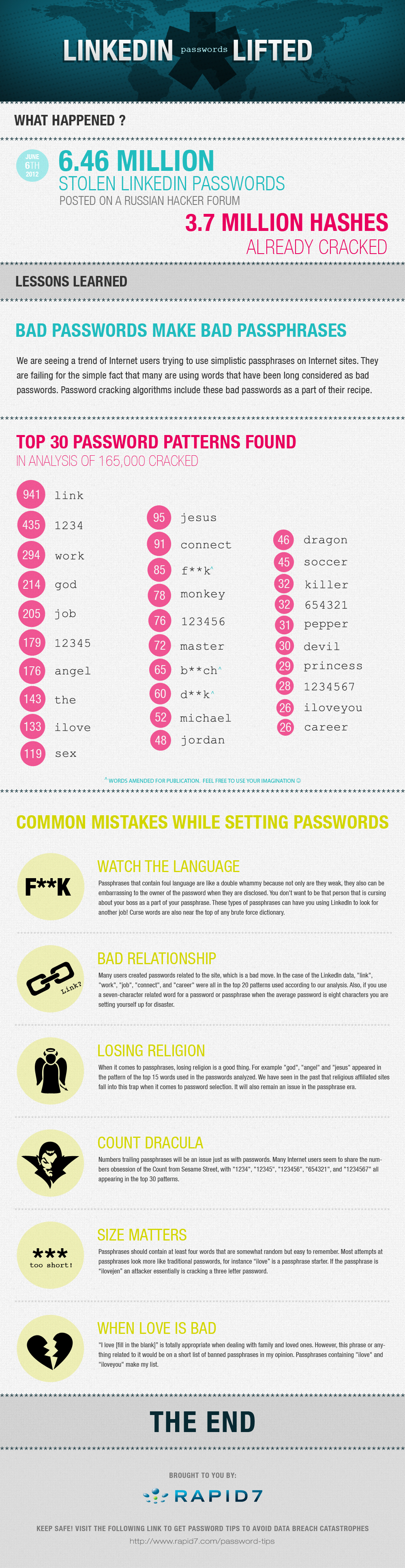
The infographic published by SecurityStreet on Visual.ly charts the lesson learned from LinkedIn’s security breach, the top 30 password patterns found in an analysis of 165,000 cracked passwords, and six common mistakes made while setting passwords.
The lesson that has been learned from this breach, according to the infographic, is bad passwords make bad passphrases. The difference between the two is that a passphrase usually includes spaces, whereas passwords do not. A password could be, for example, ‘b@tman’, and a passphrase could be ‘Here comes b@tman and Robin’.
The infographic’s look at the top 30 password patterns includes the usual suspects, such as ‘123456’, as well as some more unusual ones, such as ‘jesus’, ‘dragon’ and ‘pepper’, as well as curse words. Several of the password patterns reflect one of the most common mistakes people make when creating passwords, which is creating passwords related to the site, such as ‘career’ for LinkedIn.
LinkedIn confirmed last week that passwords found posted to the InsidePro forums were indeed from its accounts.
“We are continuing to work with law enforcement as they investigate this crime,” LinkedIn said yesterday.
“The health of our network, as measured by member growth and engagement, remains as strong as it was prior to the incident.”