The domain name servers of the New York Times, Twitter and Huffington Post UK have been hacked by the Syrian Electronic Army. The army gained access to registry records after attacking registrar Melbourne IT and took the newspaper’s site offlne after changing contact details and domain name servers.
Melbourne IT is regarded as one of the most secure DNS registrars and is used by large organisations like Twitter and the Huffington Post.
Users first began to notice problems when the New York Times web page wouldn’t load yesterday.
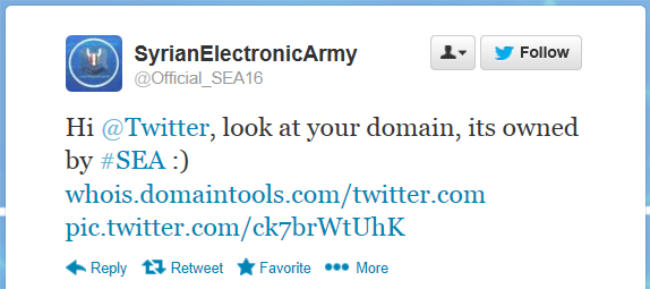
After claiming responsibility for the attack on the New York Times, the Syrian Electronic Army then began boasting that it had taken over the Twitter.com domain. This turned out to be a server related to contact details.
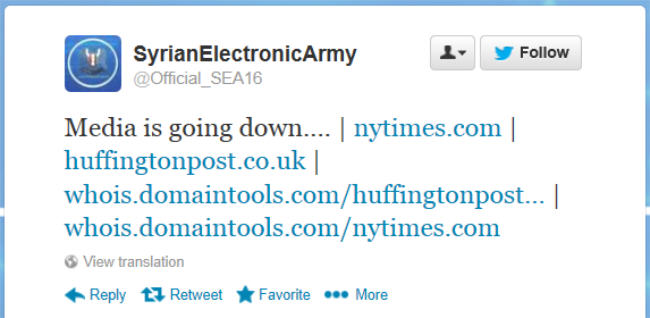
This was followed by the army claiming responsibility for both the New York Times and Huffington Post UK websites going down.
“Recursive DNS providers follow the DNS chain, starting at the root, then the TLD registry, then ultimately to whatever is listed as the authoritative name server for the domain,” CloudFlare’s Matthew Prince explained.
“In order to lighten the load upstream, recursive DNS providers cache results for a limited period of time known as a TTL. Compromising any step in the DNS chain would allow an attacker to take over some or all traffic destined for a site. That’s exactly what happened today.”
How the Syrian Electronic Army attacked NYTimes.com, HuffPo and Twitter
Prince said details of how the attack on Melbourne IT was accomplished are still sketchy.
“While we’ve been in contact with MelbourneIT, we don’t yet have details on how the attack was accomplished. We do know that the attacker was able to update the name servers for NYTimes.com without authorisation, effectively hijacking the site.
“The bad records entered by the hackers at MelbourneIT were pushed from the registrar up to the registry, Verisign, which manages the .com TLD. In particular, the NYTimes.com site had its name servers at the registry listed as ns5.boxsecured.com and ns6.boxsecured.com. The correct name servers should have been DNS.EWR1.NYTIMES.COM and DNS.SEA1.NYTIMES.COM. Troublingly, MelbourneIT initially appeared unable to correct the bad entries at the registry.
“From screen shots that the Syrian Electronic Army has subsequently posted to its Twitter feed, it appears that the hackers gained access to MelbourneIT’s administrative control panel.
“While NYT worked on getting the bad records corrected with MelbourneIT, we reached out to two of the largest recursive DNS providers: OpenDNS and Google. Technical teams from CloudFlare, OpenDNS and Google jumped on a conference call and discovered what appeared to be malware on the site, to which the NYTimes.com site was redirected. OpenDNS and Google’s DNS team worked to correct the hacked records for the customers of their recursive DNS services.”
According to Prince, Verisign has rolled back changes to the name servers and added a registry lock to NYTimes.com.
Nevertheless, it was what he believes to be a very “spooky” attack.
“The registrar of the primary domain the Syrian Electronic Army was using as a name server for the domains they hacked revoked the domain’s registration this afternoon. Since the cache TTL on the domain was relatively short, shortly after the domain was revoked traffic largely stopped flowing to the malware infected sites. That did not mean all hacked sites came back online. In some places, DNS recursors continue to have the cached bad records.
“They will expire over the next 24 hours and traffic to sites will return to normal,” Prince said.
Hacker image via Shutterstock